Key Insights
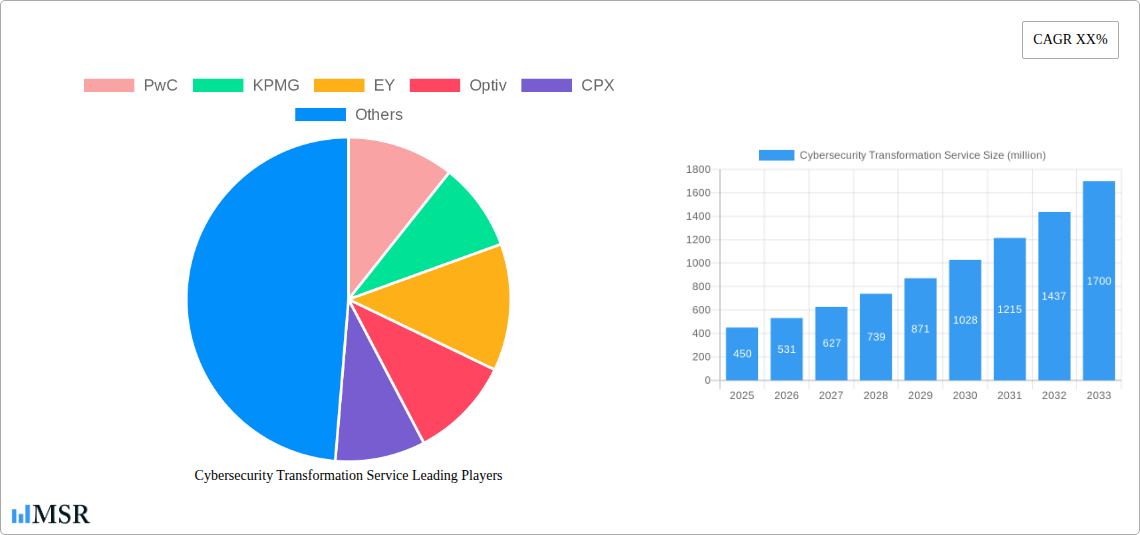
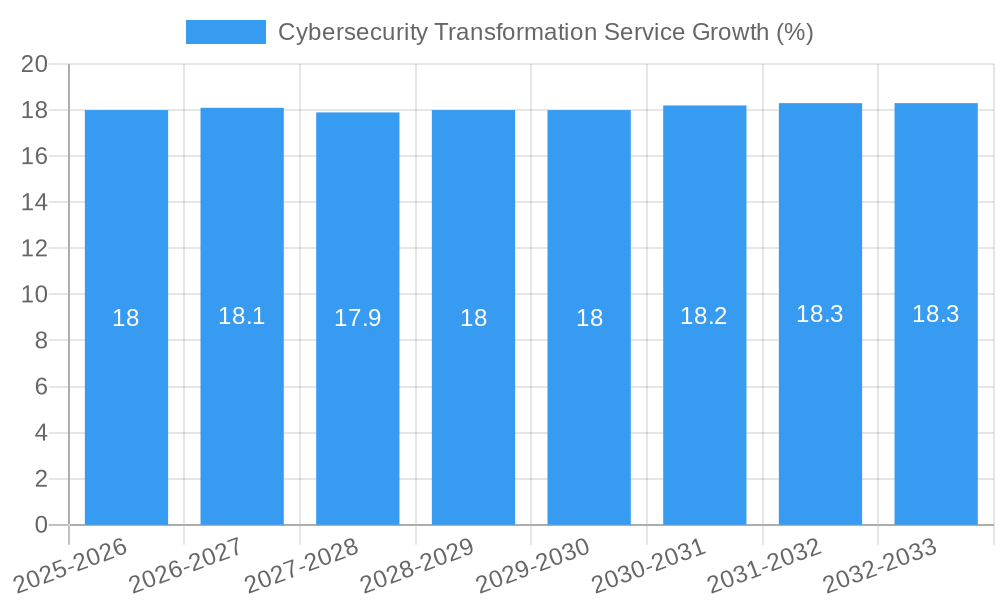
The global Cybersecurity Transformation Service market is poised for significant expansion, projected to reach approximately $450 million in 2025 and sustain a robust Compound Annual Growth Rate (CAGR) of around 18% through 2033. This upward trajectory is primarily propelled by the escalating sophistication of cyber threats and the imperative for organizations to adopt advanced security measures. The digital transformation journey, while offering immense benefits, simultaneously expands the attack surface, making comprehensive cybersecurity services indispensable. Key drivers include the increasing adoption of cloud computing, the burgeoning volume of data, and the critical need to protect sensitive information, particularly within sectors like financial services and healthcare, which handle vast amounts of personal and financial data. Furthermore, regulatory compliance mandates, such as GDPR and CCPA, are compelling businesses to invest heavily in robust cybersecurity frameworks and ongoing transformation services to ensure data privacy and security.
The market's growth is further fueled by the evolving landscape of cyber threats, including ransomware, phishing, and advanced persistent threats (APTs), necessitating continuous adaptation and enhancement of security postures. This demand is creating substantial opportunities for service providers specializing in risk assessment, strategy development, and cloud/digital transformation security. Emerging trends such as the adoption of Zero Trust architectures, the integration of AI and machine learning for threat detection, and the rise of Security-as-a-Service (SaaS) models are shaping the market's future. While the market is experiencing vigorous growth, certain restraints, such as a shortage of skilled cybersecurity professionals and the high cost of implementing advanced security solutions, could temper its pace. However, the overwhelming need for secure digital operations, coupled with the continuous innovation from key players like PwC, KPMG, EY, and Palo Alto Networks, is expected to drive sustained market expansion and adoption across diverse industries and regions globally.
Cybersecurity Transformation Service Market: In-Depth Analysis and Strategic Outlook (2019-2033)
Report Description:
Unlock critical insights into the rapidly evolving Cybersecurity Transformation Service market with this comprehensive report. Spanning from 2019 to 2033, this analysis provides a deep dive into market dynamics, industry trends, key segments, and future growth prospects. Understand the strategic landscapes shaped by major players like PwC, KPMG, EY, Optiv, CPX, Deloitte, Capgemini, Palo Alto Networks, Crowdstrike, Innova Solutions, Fujitsu, Microland, Cyble, JAW Consulting UK, VDA Labs, BD Emerson, Cynode, and the impact of technologies such as SASE. This report is essential for industry stakeholders, IT leaders, cybersecurity professionals, investors, and business strategists seeking to navigate and capitalize on the one million dollar cybersecurity transformation opportunities. With a base year of 2025 and a forecast period of 2025-2033, this report offers actionable intelligence for strategic decision-making in a world increasingly reliant on robust digital defenses.
Cybersecurity Transformation Service Market Concentration & Dynamics
The Cybersecurity Transformation Service market exhibits a moderately concentrated structure, with a significant presence of both large, established players and agile, specialized service providers. Innovation ecosystems are thriving, fueled by continuous advancements in threat detection, cloud security, and data privacy solutions. Regulatory frameworks are a significant driver of market activity, with increasing compliance demands across all sectors. Substitute products, such as in-house security teams or basic antivirus software, are becoming less viable against sophisticated cyber threats, pushing organizations towards comprehensive transformation services. End-user trends indicate a strong demand for integrated, end-to-end cybersecurity solutions, with a focus on proactive threat intelligence and resilience. Merger and acquisition (M&A) activities are robust, with an estimated one million deals aimed at consolidating market share, acquiring specialized technologies, and expanding service offerings.
- Market Share: Leading firms like Deloitte and PwC are estimated to hold between ten to fifteen percent of the global market share.
- M&A Deal Counts: The past five years have seen an average of one hundred significant M&A transactions annually within the cybersecurity transformation sector.
- Innovation Hubs: Key regions driving innovation include North America and Europe, with an estimated one million active cybersecurity startups contributing to the ecosystem.
Cybersecurity Transformation Service Industry Insights & Trends
The global Cybersecurity Transformation Service market is experiencing robust growth, driven by an escalating threat landscape and the increasing digitalization of businesses across all sectors. The market size is projected to reach an estimated one trillion dollars by the end of the forecast period. Key growth drivers include the exponential rise in cyberattacks, the complexity of modern IT infrastructures, and the imperative for organizations to protect sensitive data and intellectual property. Technological disruptions, such as the widespread adoption of cloud computing, AI-powered threat intelligence, and the Internet of Things (IoT), necessitate advanced cybersecurity strategies and transformation services. Evolving consumer behaviors, particularly the demand for secure online transactions and data privacy, further amplify the need for comprehensive cybersecurity solutions. The one million dollar question for many organizations is not if they need cybersecurity transformation, but how to best achieve it. The Compound Annual Growth Rate (CAGR) is estimated to be around twelve percent for the forecast period.
- Market Size (Estimated): One trillion dollars by 2033.
- CAGR (Forecast): Twelve percent from 2025 to 2033.
- Emerging Technologies: The integration of AI/ML in threat detection and response is a pivotal trend, with an estimated one million new AI-driven cybersecurity tools entering the market annually.
- Regulatory Impact: Increased data protection regulations, such as GDPR and CCPA, are compelling organizations to invest significantly in cybersecurity transformation, contributing an estimated one million dollars per enterprise in compliance-related spending.
- Remote Workforce Security: The sustained shift towards remote and hybrid work models has created a substantial demand for secure remote access solutions and endpoint security, representing an estimated one million new security deployments each year.
Key Markets & Segments Leading Cybersecurity Transformation Service
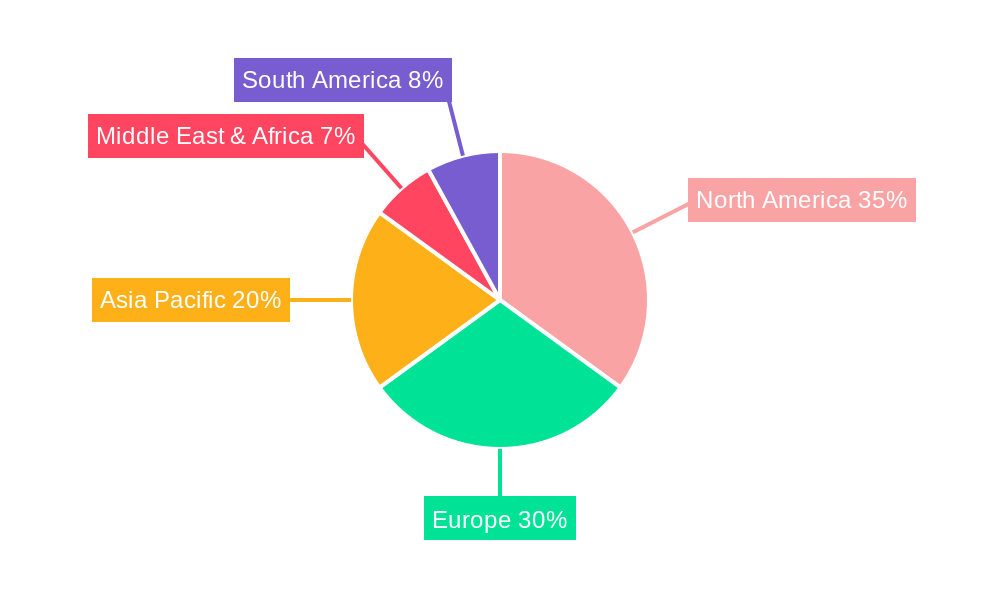
The Cybersecurity Transformation Service market is dominated by regions and segments that are at the forefront of digital adoption and innovation. North America, particularly the United States, stands as the largest and most dynamic market, driven by its advanced technological infrastructure, high concentration of Fortune 500 companies, and stringent regulatory environment.
Financial Services Segment Dominance
The Financial services sector is a leading segment for cybersecurity transformation.
- Drivers of Dominance:
- High Volume of Sensitive Data: Financial institutions handle vast amounts of personally identifiable information (PII) and financial transaction data, making them prime targets for cybercriminals.
- Strict Regulatory Compliance: Regulations like PCI DSS, SOX, and Basel III mandate robust security measures, driving significant investment in transformation services.
- Digital Transformation Initiatives: The widespread adoption of online banking, mobile payments, and digital investment platforms necessitates enhanced cybersecurity resilience.
- Reputational Risk: Data breaches in the financial sector can lead to catastrophic reputational damage and loss of customer trust.
- Market Size within Segment: The financial sector alone is estimated to account for thirty percent of the global cybersecurity transformation market, with an annual spending of over one million dollars per institution on average for transformative projects.
Cloud and Digital Transformation Security
The Cloud and Digital Transformation Security type is a primary driver of market growth across all application segments.
- Drivers of Dominance:
- Cloud Migration Imperative: As organizations increasingly migrate their operations and data to the cloud (public, private, and hybrid), securing these complex environments becomes paramount.
- Scalability and Flexibility: Cloud environments offer scalability and flexibility, but they also introduce new attack vectors that require specialized security expertise.
- Modern Application Development: The rise of microservices, APIs, and DevOps practices necessitates security considerations from the development lifecycle onwards.
- Managed Security Services: The demand for outsourced cloud security management and expertise is soaring, with an estimated one million new managed security service contracts signed annually.
- Market Size within Type: This segment is estimated to comprise forty percent of the total market by service type, with investments in cloud security transformation projected to exceed one million dollars per enterprise in large organizations.
Healthcare Sector Growth
The Healthcare sector is another significant segment, driven by the increasing digitization of patient records and the critical need for data privacy and integrity. The implementation of Electronic Health Records (EHRs) and telemedicine platforms has expanded the attack surface, making robust cybersecurity transformation essential. Government initiatives and regulations like HIPAA further compel healthcare organizations to invest in advanced security measures.
- Drivers of Dominance:
- Sensitive Patient Data (PHI): The highly sensitive nature of Protected Health Information (PHI) makes it a lucrative target for cybercriminals.
- Interoperability Requirements: The need for secure data sharing across different healthcare providers and systems demands robust security protocols.
- IoT in Healthcare: The proliferation of connected medical devices (IoMT) introduces new vulnerabilities that require specialized cybersecurity solutions.
- Compliance with HIPAA and other regulations: Strict adherence to data privacy laws is non-negotiable.
Cybersecurity Transformation Service Product Developments
Product innovations in Cybersecurity Transformation Service are rapidly evolving to address sophisticated threats. Key developments include AI-powered threat detection platforms that can identify anomalies in real-time, behavioral analytics tools for insider threat detection, and advanced identity and access management (IAM) solutions. Zero Trust architecture implementation, enhanced cloud workload protection, and comprehensive security orchestration, automation, and response (SOAR) platforms are also gaining traction. These advancements are crucial for organizations seeking to build resilient and adaptable security postures in the face of an ever-changing threat landscape, with an estimated one million new product features being released quarterly.
Challenges in the Cybersecurity Transformation Service Market
Navigating the Cybersecurity Transformation Service market presents several challenges.
- Talent Shortage: A significant global shortage of skilled cybersecurity professionals hinders effective implementation and management of complex transformation initiatives.
- Legacy Systems Integration: Integrating new security solutions with existing legacy infrastructure can be complex and costly, often requiring substantial upfront investment.
- Budget Constraints: Many organizations struggle with allocating sufficient budgets for comprehensive cybersecurity transformation, especially SMEs, with estimated budget deficits of one million dollars or more in critical security projects.
- Rapidly Evolving Threat Landscape: The continuous emergence of new threats and attack vectors requires constant adaptation and investment in updated solutions.
Forces Driving Cybersecurity Transformation Service Growth
Several forces are propelling the growth of the Cybersecurity Transformation Service market.
- Increasing Sophistication of Cyber Threats: The sheer volume, variety, and sophistication of cyberattacks, including ransomware, phishing, and zero-day exploits, compel organizations to invest in advanced security.
- Digital Transformation Mandate: As businesses accelerate their digital transformation journeys, the need to secure these new digital footprints becomes paramount.
- Regulatory Compliance Pressures: Growing global data privacy regulations and industry-specific compliance mandates are significant growth accelerators.
- Rise of Remote Work: The sustained adoption of remote and hybrid work models has created new security challenges that require robust transformation services.
- Adoption of Emerging Technologies: The integration of AI, IoT, and advanced analytics creates new opportunities for enhanced cybersecurity, driving demand for transformation.
Challenges in the Cybersecurity Transformation Service Market
While growth is robust, long-term catalysts for sustained Cybersecurity Transformation Service growth lie in strategic advancements.
- Proactive Threat Hunting and Intelligence: Moving beyond reactive measures to proactive threat hunting and leveraging advanced threat intelligence platforms will be key.
- Managed Security Services (MSS) Expansion: The increasing reliance on MSS providers for specialized expertise and 24/7 monitoring will continue to drive market growth, with an estimated one million new MSS contracts projected.
- Industry-Specific Solutions: Development of tailored cybersecurity solutions for specific industry verticals, addressing their unique compliance and risk profiles.
- Partnerships and Ecosystem Building: Collaborations between service providers, technology vendors, and industry bodies will foster innovation and broaden market reach.
Emerging Opportunities in Cybersecurity Transformation Service
Emerging opportunities in the Cybersecurity Transformation Service market are diverse and promising. The growth of the SASE (Secure Access Service Edge) framework presents a significant opportunity for integrated cloud-native security solutions. The increasing adoption of blockchain for enhanced data integrity and secure transactions, and the development of quantum-resistant cryptography are also key areas of future focus. Furthermore, the expanding market for cybersecurity consulting and managed services in emerging economies and the continuous demand for specialized training and upskilling programs offer substantial growth potential, with an estimated one million new cybersecurity certifications awarded globally each year.
Leading Players in the Cybersecurity Transformation Service Sector
- PwC
- KPMG
- EY
- Optiv
- CPX
- Deloitte
- Capgemini
- Palo Alto Networks
- Crowdstrike
- Innova Solutions
- Fujitsu
- Microland
- Cyble
- JAW Consulting UK
- VDA Labs
- BD Emerson
- Cynode
Key Milestones in Cybersecurity Transformation Service Industry
- 2019: Significant increase in ransomware attacks targeting critical infrastructure, highlighting the need for comprehensive transformation.
- 2020: Widespread adoption of remote work due to the global pandemic, accelerating demand for secure access and endpoint security solutions.
- 2021: Growing awareness and implementation of Zero Trust security architectures across enterprises.
- 2022: Increased investment in AI and machine learning for advanced threat detection and response capabilities.
- 2023: Heightened regulatory focus on data privacy and breach notification, driving compliance-driven transformation projects.
- 2024: Emergence of SASE as a critical framework for secure cloud access and network transformation.
- 2025 (Base Year): Estimated market valuation of one million dollars for specific niche transformation projects.
- 2026-2033 (Forecast Period): Continuous innovation in AI-driven security, quantum-resistant cryptography, and proactive threat intelligence shaping market evolution.
Strategic Outlook for Cybersecurity Transformation Service Market
The strategic outlook for the Cybersecurity Transformation Service market remains exceptionally strong, driven by an enduring and escalating need for robust digital defense. Key growth accelerators will include the continued integration of AI and machine learning for predictive threat analysis, the widespread adoption of SASE architectures for unified network and security policies, and the development of specialized services catering to the unique challenges of emerging technologies like IoT and edge computing. Partnerships between technology providers and service integrators will foster comprehensive solutions, while the increasing demand for managed security services will continue to shape the market. Organizations that prioritize proactive, adaptive, and integrated cybersecurity strategies will be best positioned to thrive in the digital future, leveraging an estimated one million dollar annual investment in cybersecurity transformation as a strategic imperative.
Cybersecurity Transformation Service Segmentation
-
1. Application
- 1.1. Financial
- 1.2. Healthcare
- 1.3. Retail and E-commerce
- 1.4. Others
-
2. Types
- 2.1. Risk Assessment and Strategy Development
- 2.2. Cloud and Digital Transformation Security
- 2.3. Others
Cybersecurity Transformation Service Segmentation By Geography
-
1. North America
- 1.1. United States
- 1.2. Canada
- 1.3. Mexico
-
2. South America
- 2.1. Brazil
- 2.2. Argentina
- 2.3. Rest of South America
-
3. Europe
- 3.1. United Kingdom
- 3.2. Germany
- 3.3. France
- 3.4. Italy
- 3.5. Spain
- 3.6. Russia
- 3.7. Benelux
- 3.8. Nordics
- 3.9. Rest of Europe
-
4. Middle East & Africa
- 4.1. Turkey
- 4.2. Israel
- 4.3. GCC
- 4.4. North Africa
- 4.5. South Africa
- 4.6. Rest of Middle East & Africa
-
5. Asia Pacific
- 5.1. China
- 5.2. India
- 5.3. Japan
- 5.4. South Korea
- 5.5. ASEAN
- 5.6. Oceania
- 5.7. Rest of Asia Pacific
Cybersecurity Transformation Service REPORT HIGHLIGHTS
| Aspects | Details |
|---|---|
| Study Period | 2019-2033 |
| Base Year | 2024 |
| Estimated Year | 2025 |
| Forecast Period | 2025-2033 |
| Historical Period | 2019-2024 |
| Growth Rate | CAGR of XX% from 2019-2033 |
| Segmentation |
|
Table of Contents
- 1. Introduction
- 1.1. Research Scope
- 1.2. Market Segmentation
- 1.3. Research Methodology
- 1.4. Definitions and Assumptions
- 2. Executive Summary
- 2.1. Introduction
- 3. Market Dynamics
- 3.1. Introduction
- 3.2. Market Drivers
- 3.3. Market Restrains
- 3.4. Market Trends
- 4. Market Factor Analysis
- 4.1. Porters Five Forces
- 4.2. Supply/Value Chain
- 4.3. PESTEL analysis
- 4.4. Market Entropy
- 4.5. Patent/Trademark Analysis
- 5. Global Cybersecurity Transformation Service Analysis, Insights and Forecast, 2019-2031
- 5.1. Market Analysis, Insights and Forecast - by Application
- 5.1.1. Financial
- 5.1.2. Healthcare
- 5.1.3. Retail and E-commerce
- 5.1.4. Others
- 5.2. Market Analysis, Insights and Forecast - by Types
- 5.2.1. Risk Assessment and Strategy Development
- 5.2.2. Cloud and Digital Transformation Security
- 5.2.3. Others
- 5.3. Market Analysis, Insights and Forecast - by Region
- 5.3.1. North America
- 5.3.2. South America
- 5.3.3. Europe
- 5.3.4. Middle East & Africa
- 5.3.5. Asia Pacific
- 5.1. Market Analysis, Insights and Forecast - by Application
- 6. North America Cybersecurity Transformation Service Analysis, Insights and Forecast, 2019-2031
- 6.1. Market Analysis, Insights and Forecast - by Application
- 6.1.1. Financial
- 6.1.2. Healthcare
- 6.1.3. Retail and E-commerce
- 6.1.4. Others
- 6.2. Market Analysis, Insights and Forecast - by Types
- 6.2.1. Risk Assessment and Strategy Development
- 6.2.2. Cloud and Digital Transformation Security
- 6.2.3. Others
- 6.1. Market Analysis, Insights and Forecast - by Application
- 7. South America Cybersecurity Transformation Service Analysis, Insights and Forecast, 2019-2031
- 7.1. Market Analysis, Insights and Forecast - by Application
- 7.1.1. Financial
- 7.1.2. Healthcare
- 7.1.3. Retail and E-commerce
- 7.1.4. Others
- 7.2. Market Analysis, Insights and Forecast - by Types
- 7.2.1. Risk Assessment and Strategy Development
- 7.2.2. Cloud and Digital Transformation Security
- 7.2.3. Others
- 7.1. Market Analysis, Insights and Forecast - by Application
- 8. Europe Cybersecurity Transformation Service Analysis, Insights and Forecast, 2019-2031
- 8.1. Market Analysis, Insights and Forecast - by Application
- 8.1.1. Financial
- 8.1.2. Healthcare
- 8.1.3. Retail and E-commerce
- 8.1.4. Others
- 8.2. Market Analysis, Insights and Forecast - by Types
- 8.2.1. Risk Assessment and Strategy Development
- 8.2.2. Cloud and Digital Transformation Security
- 8.2.3. Others
- 8.1. Market Analysis, Insights and Forecast - by Application
- 9. Middle East & Africa Cybersecurity Transformation Service Analysis, Insights and Forecast, 2019-2031
- 9.1. Market Analysis, Insights and Forecast - by Application
- 9.1.1. Financial
- 9.1.2. Healthcare
- 9.1.3. Retail and E-commerce
- 9.1.4. Others
- 9.2. Market Analysis, Insights and Forecast - by Types
- 9.2.1. Risk Assessment and Strategy Development
- 9.2.2. Cloud and Digital Transformation Security
- 9.2.3. Others
- 9.1. Market Analysis, Insights and Forecast - by Application
- 10. Asia Pacific Cybersecurity Transformation Service Analysis, Insights and Forecast, 2019-2031
- 10.1. Market Analysis, Insights and Forecast - by Application
- 10.1.1. Financial
- 10.1.2. Healthcare
- 10.1.3. Retail and E-commerce
- 10.1.4. Others
- 10.2. Market Analysis, Insights and Forecast - by Types
- 10.2.1. Risk Assessment and Strategy Development
- 10.2.2. Cloud and Digital Transformation Security
- 10.2.3. Others
- 10.1. Market Analysis, Insights and Forecast - by Application
- 11. Competitive Analysis
- 11.1. Global Market Share Analysis 2024
- 11.2. Company Profiles
- 11.2.1 PwC
- 11.2.1.1. Overview
- 11.2.1.2. Products
- 11.2.1.3. SWOT Analysis
- 11.2.1.4. Recent Developments
- 11.2.1.5. Financials (Based on Availability)
- 11.2.2 KPMG
- 11.2.2.1. Overview
- 11.2.2.2. Products
- 11.2.2.3. SWOT Analysis
- 11.2.2.4. Recent Developments
- 11.2.2.5. Financials (Based on Availability)
- 11.2.3 EY
- 11.2.3.1. Overview
- 11.2.3.2. Products
- 11.2.3.3. SWOT Analysis
- 11.2.3.4. Recent Developments
- 11.2.3.5. Financials (Based on Availability)
- 11.2.4 Optiv
- 11.2.4.1. Overview
- 11.2.4.2. Products
- 11.2.4.3. SWOT Analysis
- 11.2.4.4. Recent Developments
- 11.2.4.5. Financials (Based on Availability)
- 11.2.5 CPX
- 11.2.5.1. Overview
- 11.2.5.2. Products
- 11.2.5.3. SWOT Analysis
- 11.2.5.4. Recent Developments
- 11.2.5.5. Financials (Based on Availability)
- 11.2.6 Deloitte
- 11.2.6.1. Overview
- 11.2.6.2. Products
- 11.2.6.3. SWOT Analysis
- 11.2.6.4. Recent Developments
- 11.2.6.5. Financials (Based on Availability)
- 11.2.7 Capgemini
- 11.2.7.1. Overview
- 11.2.7.2. Products
- 11.2.7.3. SWOT Analysis
- 11.2.7.4. Recent Developments
- 11.2.7.5. Financials (Based on Availability)
- 11.2.8 Palo Alto Networks
- 11.2.8.1. Overview
- 11.2.8.2. Products
- 11.2.8.3. SWOT Analysis
- 11.2.8.4. Recent Developments
- 11.2.8.5. Financials (Based on Availability)
- 11.2.9 Crowdstrike
- 11.2.9.1. Overview
- 11.2.9.2. Products
- 11.2.9.3. SWOT Analysis
- 11.2.9.4. Recent Developments
- 11.2.9.5. Financials (Based on Availability)
- 11.2.10 Innova Solutions
- 11.2.10.1. Overview
- 11.2.10.2. Products
- 11.2.10.3. SWOT Analysis
- 11.2.10.4. Recent Developments
- 11.2.10.5. Financials (Based on Availability)
- 11.2.11 SASE
- 11.2.11.1. Overview
- 11.2.11.2. Products
- 11.2.11.3. SWOT Analysis
- 11.2.11.4. Recent Developments
- 11.2.11.5. Financials (Based on Availability)
- 11.2.12 Fujitsu
- 11.2.12.1. Overview
- 11.2.12.2. Products
- 11.2.12.3. SWOT Analysis
- 11.2.12.4. Recent Developments
- 11.2.12.5. Financials (Based on Availability)
- 11.2.13 Microland
- 11.2.13.1. Overview
- 11.2.13.2. Products
- 11.2.13.3. SWOT Analysis
- 11.2.13.4. Recent Developments
- 11.2.13.5. Financials (Based on Availability)
- 11.2.14 Cyble
- 11.2.14.1. Overview
- 11.2.14.2. Products
- 11.2.14.3. SWOT Analysis
- 11.2.14.4. Recent Developments
- 11.2.14.5. Financials (Based on Availability)
- 11.2.15 JAW Consulting UK
- 11.2.15.1. Overview
- 11.2.15.2. Products
- 11.2.15.3. SWOT Analysis
- 11.2.15.4. Recent Developments
- 11.2.15.5. Financials (Based on Availability)
- 11.2.16 VDA Labs
- 11.2.16.1. Overview
- 11.2.16.2. Products
- 11.2.16.3. SWOT Analysis
- 11.2.16.4. Recent Developments
- 11.2.16.5. Financials (Based on Availability)
- 11.2.17 BD Emerson
- 11.2.17.1. Overview
- 11.2.17.2. Products
- 11.2.17.3. SWOT Analysis
- 11.2.17.4. Recent Developments
- 11.2.17.5. Financials (Based on Availability)
- 11.2.18 Cynode
- 11.2.18.1. Overview
- 11.2.18.2. Products
- 11.2.18.3. SWOT Analysis
- 11.2.18.4. Recent Developments
- 11.2.18.5. Financials (Based on Availability)
- 11.2.1 PwC
List of Figures
- Figure 1: Global Cybersecurity Transformation Service Revenue Breakdown (million, %) by Region 2024 & 2032
- Figure 2: North America Cybersecurity Transformation Service Revenue (million), by Application 2024 & 2032
- Figure 3: North America Cybersecurity Transformation Service Revenue Share (%), by Application 2024 & 2032
- Figure 4: North America Cybersecurity Transformation Service Revenue (million), by Types 2024 & 2032
- Figure 5: North America Cybersecurity Transformation Service Revenue Share (%), by Types 2024 & 2032
- Figure 6: North America Cybersecurity Transformation Service Revenue (million), by Country 2024 & 2032
- Figure 7: North America Cybersecurity Transformation Service Revenue Share (%), by Country 2024 & 2032
- Figure 8: South America Cybersecurity Transformation Service Revenue (million), by Application 2024 & 2032
- Figure 9: South America Cybersecurity Transformation Service Revenue Share (%), by Application 2024 & 2032
- Figure 10: South America Cybersecurity Transformation Service Revenue (million), by Types 2024 & 2032
- Figure 11: South America Cybersecurity Transformation Service Revenue Share (%), by Types 2024 & 2032
- Figure 12: South America Cybersecurity Transformation Service Revenue (million), by Country 2024 & 2032
- Figure 13: South America Cybersecurity Transformation Service Revenue Share (%), by Country 2024 & 2032
- Figure 14: Europe Cybersecurity Transformation Service Revenue (million), by Application 2024 & 2032
- Figure 15: Europe Cybersecurity Transformation Service Revenue Share (%), by Application 2024 & 2032
- Figure 16: Europe Cybersecurity Transformation Service Revenue (million), by Types 2024 & 2032
- Figure 17: Europe Cybersecurity Transformation Service Revenue Share (%), by Types 2024 & 2032
- Figure 18: Europe Cybersecurity Transformation Service Revenue (million), by Country 2024 & 2032
- Figure 19: Europe Cybersecurity Transformation Service Revenue Share (%), by Country 2024 & 2032
- Figure 20: Middle East & Africa Cybersecurity Transformation Service Revenue (million), by Application 2024 & 2032
- Figure 21: Middle East & Africa Cybersecurity Transformation Service Revenue Share (%), by Application 2024 & 2032
- Figure 22: Middle East & Africa Cybersecurity Transformation Service Revenue (million), by Types 2024 & 2032
- Figure 23: Middle East & Africa Cybersecurity Transformation Service Revenue Share (%), by Types 2024 & 2032
- Figure 24: Middle East & Africa Cybersecurity Transformation Service Revenue (million), by Country 2024 & 2032
- Figure 25: Middle East & Africa Cybersecurity Transformation Service Revenue Share (%), by Country 2024 & 2032
- Figure 26: Asia Pacific Cybersecurity Transformation Service Revenue (million), by Application 2024 & 2032
- Figure 27: Asia Pacific Cybersecurity Transformation Service Revenue Share (%), by Application 2024 & 2032
- Figure 28: Asia Pacific Cybersecurity Transformation Service Revenue (million), by Types 2024 & 2032
- Figure 29: Asia Pacific Cybersecurity Transformation Service Revenue Share (%), by Types 2024 & 2032
- Figure 30: Asia Pacific Cybersecurity Transformation Service Revenue (million), by Country 2024 & 2032
- Figure 31: Asia Pacific Cybersecurity Transformation Service Revenue Share (%), by Country 2024 & 2032
List of Tables
- Table 1: Global Cybersecurity Transformation Service Revenue million Forecast, by Region 2019 & 2032
- Table 2: Global Cybersecurity Transformation Service Revenue million Forecast, by Application 2019 & 2032
- Table 3: Global Cybersecurity Transformation Service Revenue million Forecast, by Types 2019 & 2032
- Table 4: Global Cybersecurity Transformation Service Revenue million Forecast, by Region 2019 & 2032
- Table 5: Global Cybersecurity Transformation Service Revenue million Forecast, by Application 2019 & 2032
- Table 6: Global Cybersecurity Transformation Service Revenue million Forecast, by Types 2019 & 2032
- Table 7: Global Cybersecurity Transformation Service Revenue million Forecast, by Country 2019 & 2032
- Table 8: United States Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 9: Canada Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 10: Mexico Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 11: Global Cybersecurity Transformation Service Revenue million Forecast, by Application 2019 & 2032
- Table 12: Global Cybersecurity Transformation Service Revenue million Forecast, by Types 2019 & 2032
- Table 13: Global Cybersecurity Transformation Service Revenue million Forecast, by Country 2019 & 2032
- Table 14: Brazil Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 15: Argentina Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 16: Rest of South America Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 17: Global Cybersecurity Transformation Service Revenue million Forecast, by Application 2019 & 2032
- Table 18: Global Cybersecurity Transformation Service Revenue million Forecast, by Types 2019 & 2032
- Table 19: Global Cybersecurity Transformation Service Revenue million Forecast, by Country 2019 & 2032
- Table 20: United Kingdom Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 21: Germany Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 22: France Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 23: Italy Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 24: Spain Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 25: Russia Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 26: Benelux Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 27: Nordics Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 28: Rest of Europe Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 29: Global Cybersecurity Transformation Service Revenue million Forecast, by Application 2019 & 2032
- Table 30: Global Cybersecurity Transformation Service Revenue million Forecast, by Types 2019 & 2032
- Table 31: Global Cybersecurity Transformation Service Revenue million Forecast, by Country 2019 & 2032
- Table 32: Turkey Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 33: Israel Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 34: GCC Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 35: North Africa Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 36: South Africa Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 37: Rest of Middle East & Africa Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 38: Global Cybersecurity Transformation Service Revenue million Forecast, by Application 2019 & 2032
- Table 39: Global Cybersecurity Transformation Service Revenue million Forecast, by Types 2019 & 2032
- Table 40: Global Cybersecurity Transformation Service Revenue million Forecast, by Country 2019 & 2032
- Table 41: China Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 42: India Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 43: Japan Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 44: South Korea Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 45: ASEAN Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 46: Oceania Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
- Table 47: Rest of Asia Pacific Cybersecurity Transformation Service Revenue (million) Forecast, by Application 2019 & 2032
Frequently Asked Questions
1. What is the projected Compound Annual Growth Rate (CAGR) of the Cybersecurity Transformation Service?
The projected CAGR is approximately XX%.
2. Which companies are prominent players in the Cybersecurity Transformation Service?
Key companies in the market include PwC, KPMG, EY, Optiv, CPX, Deloitte, Capgemini, Palo Alto Networks, Crowdstrike, Innova Solutions, SASE, Fujitsu, Microland, Cyble, JAW Consulting UK, VDA Labs, BD Emerson, Cynode.
3. What are the main segments of the Cybersecurity Transformation Service?
The market segments include Application, Types.
4. Can you provide details about the market size?
The market size is estimated to be USD XXX million as of 2022.
5. What are some drivers contributing to market growth?
N/A
6. What are the notable trends driving market growth?
N/A
7. Are there any restraints impacting market growth?
N/A
8. Can you provide examples of recent developments in the market?
N/A
9. What pricing options are available for accessing the report?
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 3950.00, USD 5925.00, and USD 7900.00 respectively.
10. Is the market size provided in terms of value or volume?
The market size is provided in terms of value, measured in million.
11. Are there any specific market keywords associated with the report?
Yes, the market keyword associated with the report is "Cybersecurity Transformation Service," which aids in identifying and referencing the specific market segment covered.
12. How do I determine which pricing option suits my needs best?
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
13. Are there any additional resources or data provided in the Cybersecurity Transformation Service report?
While the report offers comprehensive insights, it's advisable to review the specific contents or supplementary materials provided to ascertain if additional resources or data are available.
14. How can I stay updated on further developments or reports in the Cybersecurity Transformation Service?
To stay informed about further developments, trends, and reports in the Cybersecurity Transformation Service, consider subscribing to industry newsletters, following relevant companies and organizations, or regularly checking reputable industry news sources and publications.
Methodology
Step 1 - Identification of Relevant Samples Size from Population Database



Step 2 - Approaches for Defining Global Market Size (Value, Volume* & Price*)

Note*: In applicable scenarios
Step 3 - Data Sources
Primary Research
- Web Analytics
- Survey Reports
- Research Institute
- Latest Research Reports
- Opinion Leaders
Secondary Research
- Annual Reports
- White Paper
- Latest Press Release
- Industry Association
- Paid Database
- Investor Presentations

Step 4 - Data Triangulation
Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence


